Outcome
Scaled user verification from an on-platform feature into durable identity infrastructure (largest among major platforms), benefiting members, partners, and the broader ecosystem.
Strategy
Opportunity
AI made it easy to pretend to be someone you're not. Fake resumes, fake profiles, fake experts. LinkedIn already connects real people to real jobs, companies, and credentials. We were uniquely positioned to address this at scale.
Approach
Scaling verification off-platform without diluting trust or over-collecting data. Keeping verification free made it viable as shared infrastructure rather than a gated feature.
Keeping verification free for everyone enabled:
Network effects
Portable verification increased trust and engagement as adoption grew
Strategic moat
Defensible, partner-aware identity beyond a single platform
Future revenue
A foundation for B2B API monetization once infrastructure was established
Findings & Risks
Research and risk workshops refined the strategy. They informed our principles, consent tiering, badge design, partner criteria, and API model.
Key findings
A single signal needs to be elastic
Instant reassurance for low-stakes moments. Deep credibility when it matters most.
Protect the network: Trust doesn't transfer
You can't just plug identity signals from one ecosystem into another without diluting the entire brand.
Risks
Risk
Trust breaks down when verification is scarce or inconsistent.
De-risk
Strict partner criteria. Protect existing trust signals, avoid brand dilution and bad press.
Risk
Privacy and regulatory risk increased when partners handled identity data themselves
De-risk
Kill-switch architecture to prevent misuse or spoofed badges
Risk
Verification stuck inside LinkedIn limits platform value.
De-risk
Beta with 5 vetted partners. Stress-test the UX, API, and business assumptions before scaling.
Key Decisions
Self-Serve vs. Contract-Only
Tension
Business wanted quality control, Engineering wanted scale, Legal/Brand wanted guardrails.
Decision: Both/Phased
Launch with vetted partners to validate trust patterns, then expand to self-serve once safeguards were established.
Outcome
Self-serve API launched Dec 2025 with tiered access (Development vs. Plus). Scale with safety, not one or the other.
Safety Signal vs. Marketing
Tension
Marketing pushed for prominent branding; Legal wanted explicit technical language; partners wanted flexibility.
Decision: Safety Signal
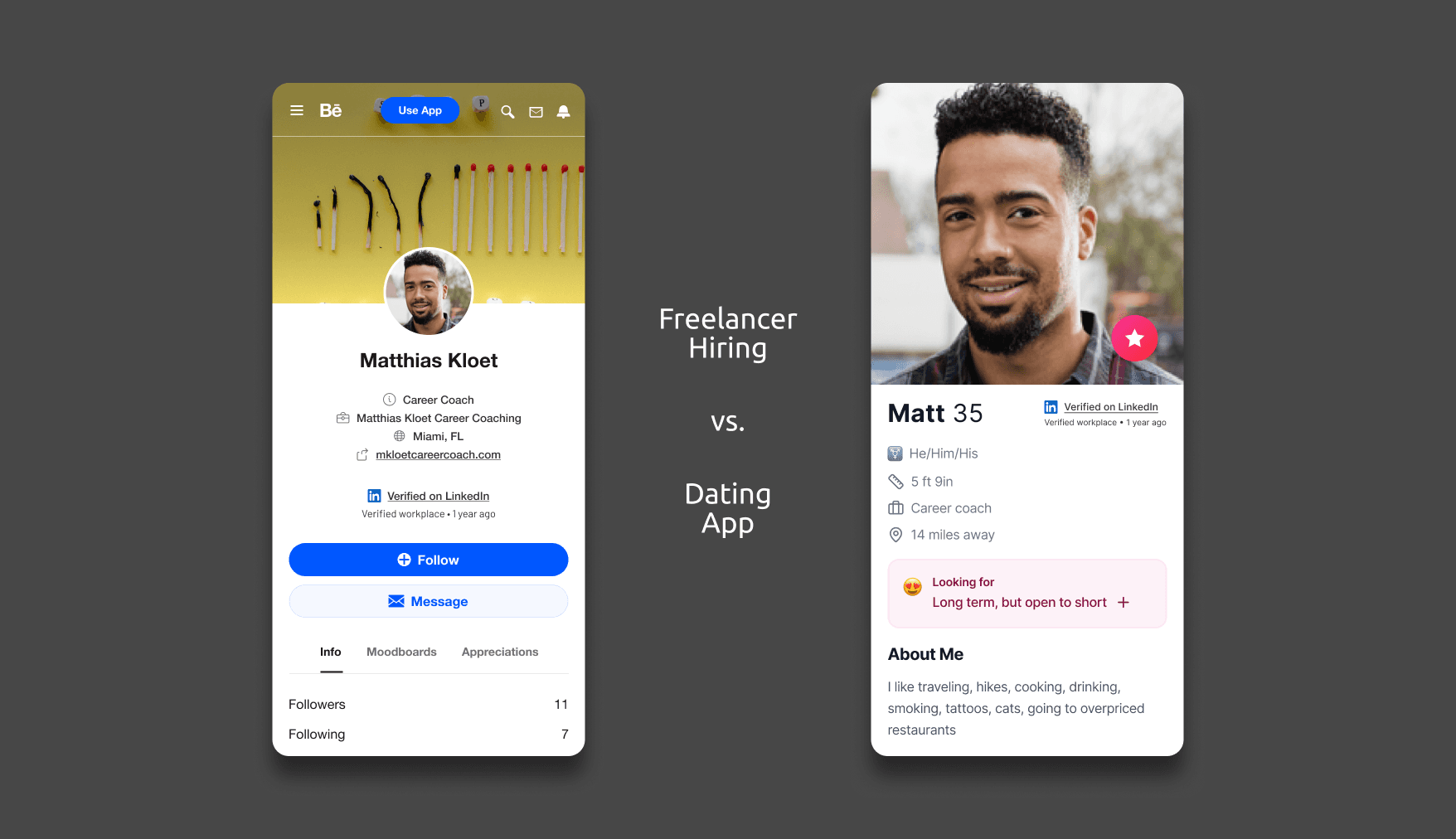
A subtle, credibility-first badge ("Verified on LinkedIn") that behaved like a safety signal, not an ad. Users trusted verification more when it felt protective, not promotional.
Outcome
Partners like Adobe integrated specifically because of badge credibility.
Fixed vs. Adaptive Data
Tension
Partners needed different trust depth; a single access level either over-exposed data or limited usefulness.
Decision: Adaptive
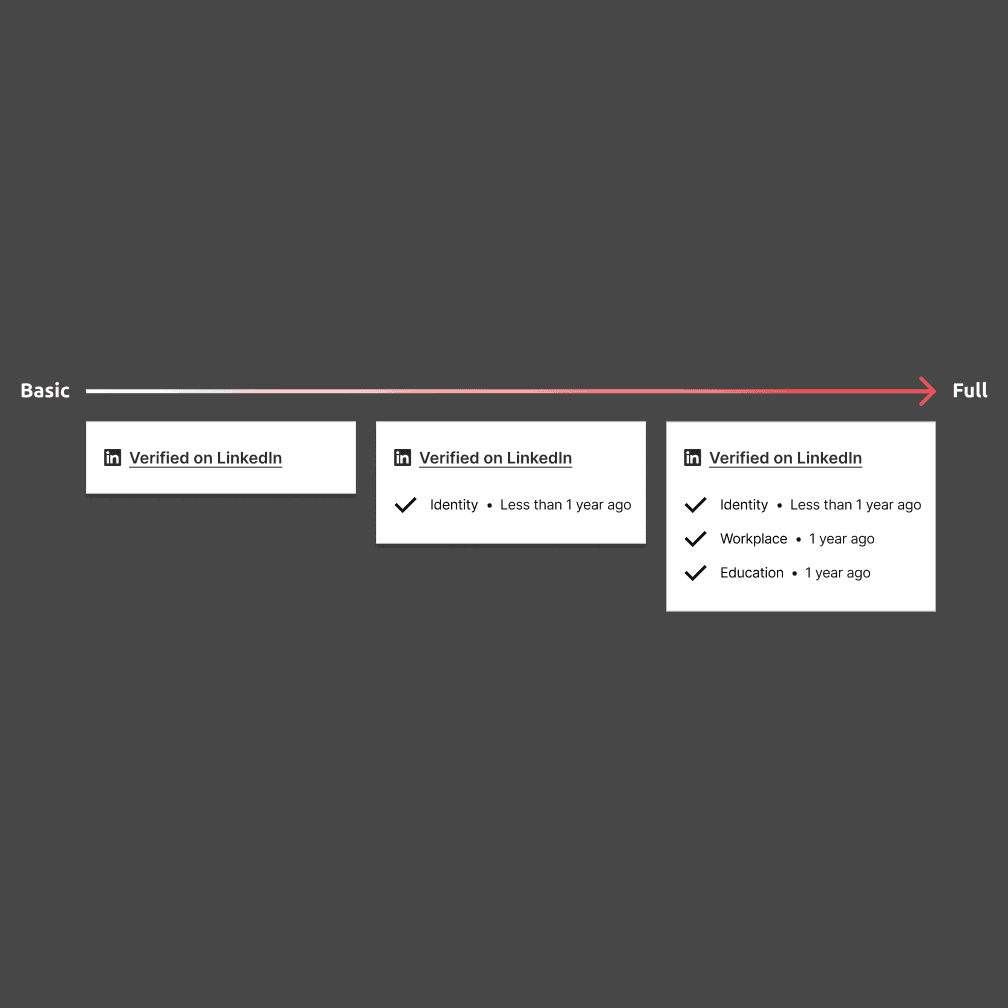
Three-tier consent model adapting verification depth by use case: Basic (yes/no), Standard (verification type), Full (details with explicit consent).
Outcome
This adaptive model became the standard for future LinkedIn API products.
My Deliverables
API Partner Playbook
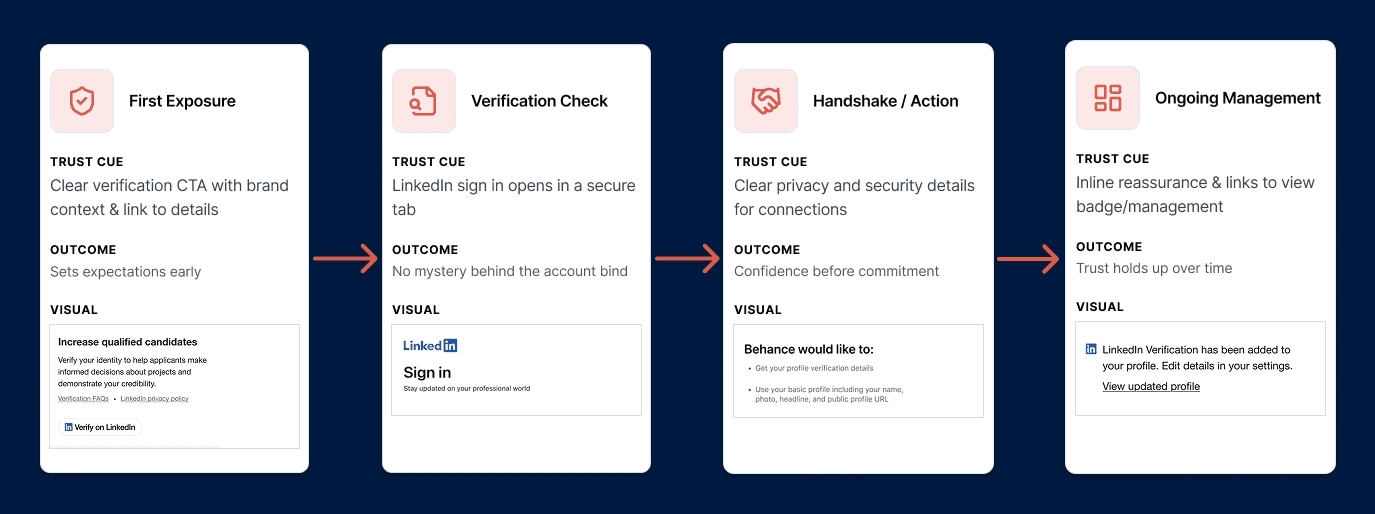
Digital document including logo variations and files, content guidelines, flows for onboarding, etc.
Verification Governance Model
Defined when to verify, how to display trust signals, and when to revoke—now used across LinkedIn trust products.
My Role
Project responsibilities:
Off-platform verification lead: Strategy, governance, partner experience
Cross-functional orchestration: Aligned engineering, legal, product teams
Business development: Design liaison in partner negotiations, UX as deal differentiator
Scaled impact: Partner playbooks adopted across 8+ integrations
Unified strategy: Consolidated on/off-platform verification into single system
At scale, strategy is the most important craft. The badge mattered. The infrastructure mattered more.